Learn CyberOps Test iOS App
Master the Cyber Operations landscape with Learn CyberOps Test! Our app is expertly tailored to immerse you in a robust testing environment, offering a broad spectrum of practice questions that touch on every critical aspect necessary for Cyber Operations certification.
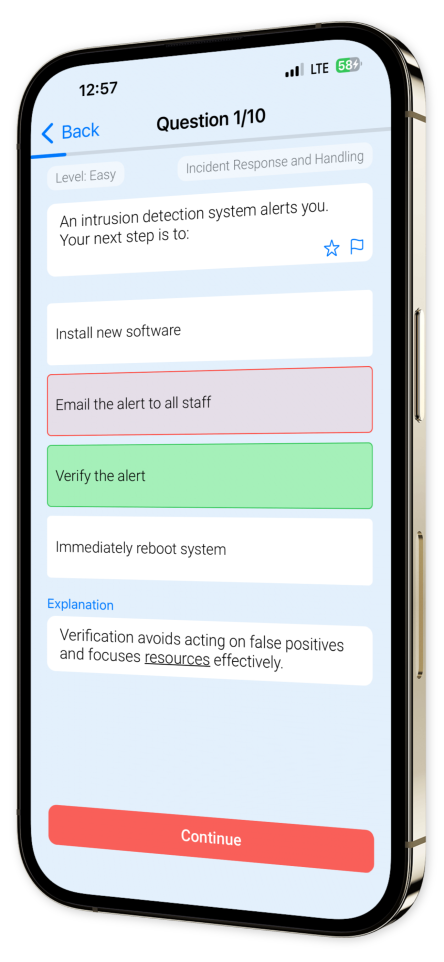
Each question is paired with comprehensive explanations to deepen your understanding and refine your expertise.
Key Features:
Extensive Question Bank: Dive into a vast collection of questions covering vital topics to ensure a well-rounded preparation.
In-Depth Explanations: Unlock insights from every question with detailed explanations to boost your learning and retention.
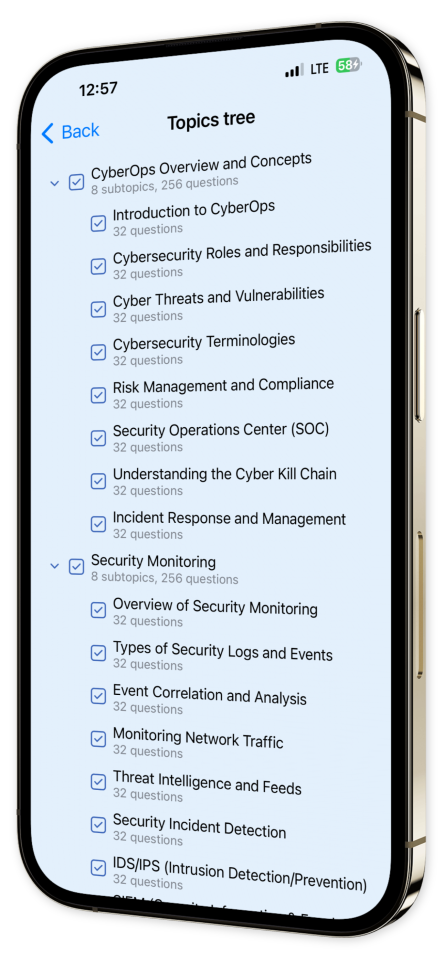
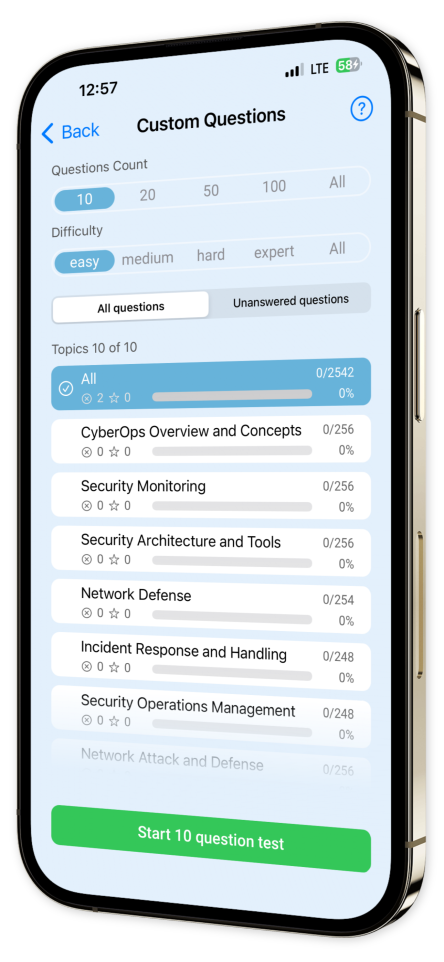
Custom Test Creation: Tailor your quizzes by choosing specific topics and question types, enabling you to concentrate on your areas of need.
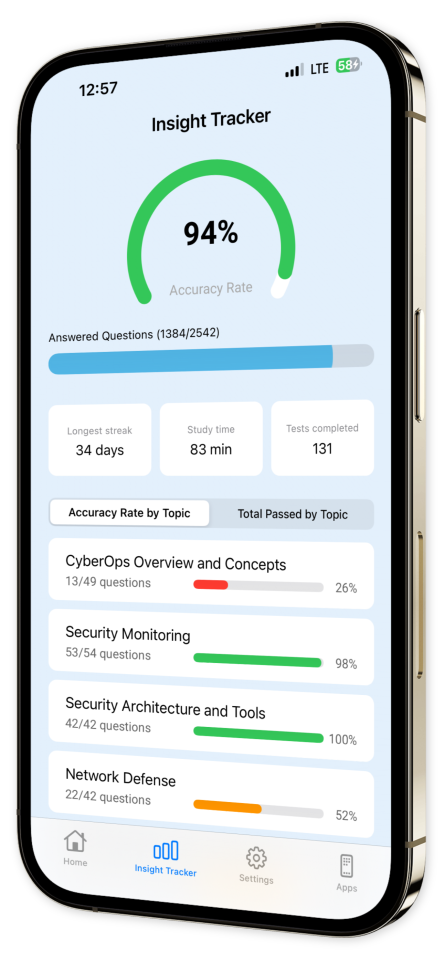
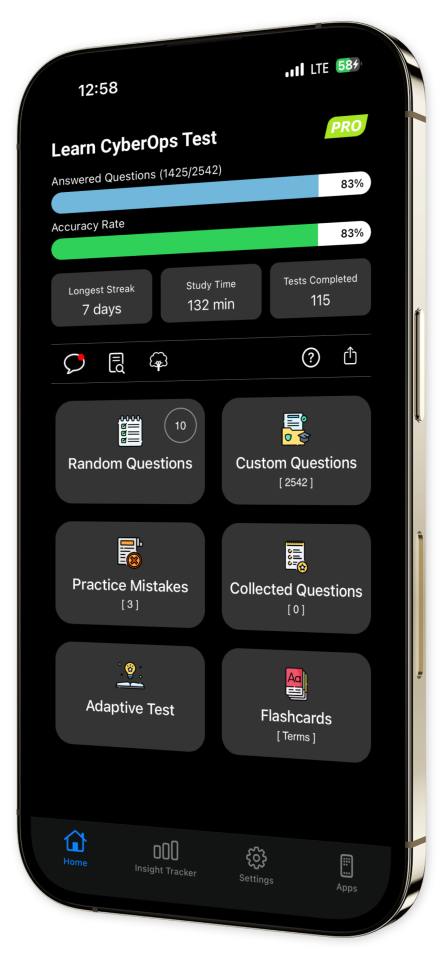
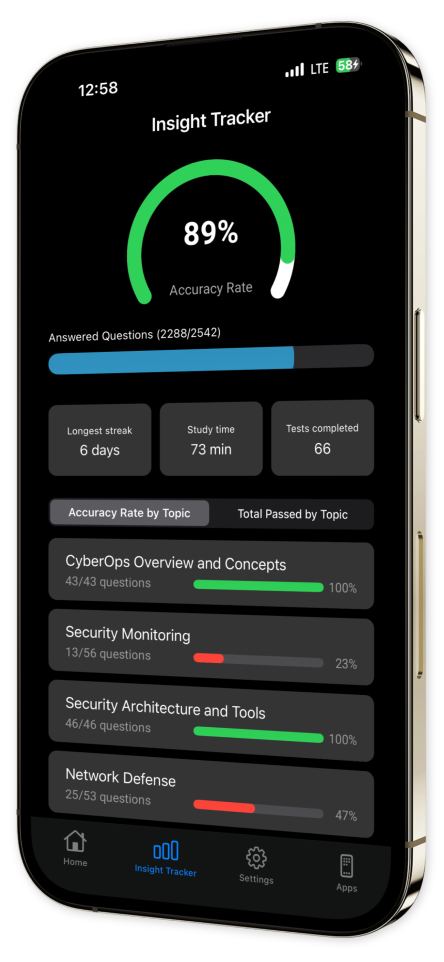
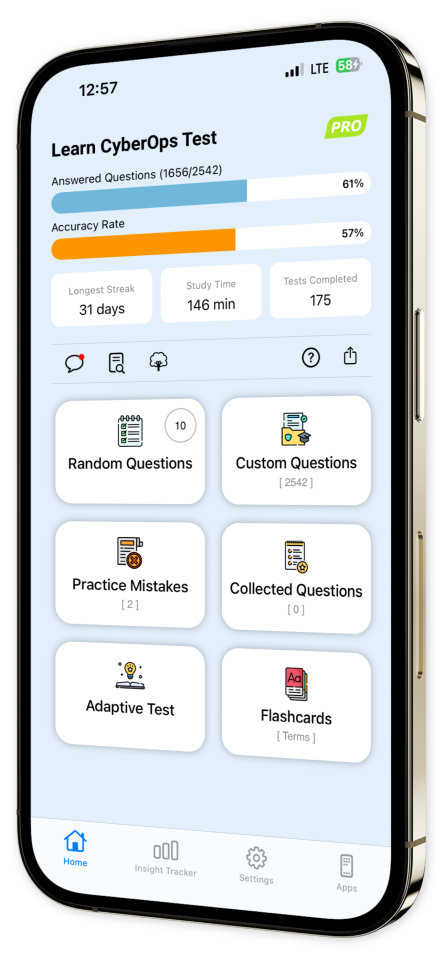
Progress Tracking: Monitor your advancement over time with our easy-to-use progress tracking tools.
Offline Access: Study whenever and wherever, even without an internet connection - ideal for on-the-go learning.
User-Friendly Interface: Enjoy a seamless and intuitive app experience that keeps your focus on acing the material.
Download Learn CyberOps Test today and dive into a smarter, more effective approach to preparing for your Cyber Operations certification. Elevate your knowledge, enhance your skills, and conquer your CyberOps exam with confidence. Join the countless users who have transformed their study routine with Learn CyberOps Test!
Content Overview
Explore a variety of topics covered in the app.
Example questions
Let's look at some sample questions
What is the primary goal of cybersecurity operations?
To protect information systemsTo hack into secure networksTo create new virusesTo bypass firewalls
The goal of CyberOps is to protect information systems from unauthorized access or attacks.
Which of the following is a fundamental step in a CyberOps monitoring strategy?
Installing antivirusIdentifying anomaliesRunning regular updatesEmployee training
Identifying anomalies is crucial for detecting unusual activities that could indicate security issues.
What is a potential impact of a DDoS attack on a network?
Data breachUnauthorized accessService unavailabilityData corruption
DDoS attacks overwhelm network resources, causing service unavailability rather than data breaches or corruption.
Which of the following is a zero-day vulnerability?
Publicly known flawFlaw with available patchUndiscovered flawUser-reported bug
Zero-day vulnerability is an undiscovered flaw with no available patch, making it a prime target for attackers.
What term describes software with embedded security flaws that are not exploited yet?
Zero-day VulnerabilityBackdoorTrojan HorseMalware
Zero-day vulnerabilities refer to security flaws that are not yet known to the software vendor and remain unexploited, waiting to be discovered.
What is the primary goal of a Denial of Service (DoS) attack?
Steal sensitive dataDisrupt normal service operationsCorrupt databasesSpy on network traffic
A DoS attack aims to make a service unavailable, disrupting operations by overwhelming it with traffic.
Which term describes an attacker gaining unauthorized access to a device to manipulate data?
SniffingHackingPhishingSpoofing
Hacking involves unauthorized access to systems or networks to steal, alter, or damage information.
Calculate the block encryption time for 10 blocks, each 128 bits, at 1000 bps.
1.28 seconds13 seconds15.36 seconds33 seconds
Each block (128 bits) needs 0.128 seconds (128/1000), totaling 1.28 seconds for one block. For 10 blocks, 1.28 * 10 = 12.8 seconds, verified as consistent.
What is an appropriate defense against eavesdropping on internal network traffic?
Use VLANsCross-site ScriptingIP WhitelistingZero Trust
Using VLANs can segment network traffic, limiting the exposure to eavesdropping within an internal network. This is validated by network security best practices.
Which of the following technologies uses heuristic analysis to detect malware?
Signature-based detectionFirewallAntivirus softwareIntrusion Detection System (IDS)
Antivirus software may utilize heuristic analysis to identify new or modified malware by examining characteristics and behaviors, beyond known signatures.